> |
> That's me working on the next big thing!Delivery comms, intelligent fulfilment, and AI’s growing influence /Iranian hacktivists muster their forces but state APTs lay low /Zero-day in Android phone chips under active attack /Tycoon2FA phishing platform dismantled in major operation /UK lab gets funding to drive foundational AI research /Landmark legal challenge against Home Office eVisa system heard /Is there no stopping the AI spending spree? /Civil service veteran ‘incandescent’ as wait for pension hits four months amid outsourcing mess /AI workloads force a fundamental redesign of Middle East datacentres /Transnational AI regulation needed to protect human rights in the UK /National Grid, Nebius and Emerald hail datacentre power throttling /Interview: Wolf & Badger CEO George Graham on getting ‘hands-on’ with AI /Open cyber standards key to cross-platform integration /Santander and Mastercard complete test of AI-initiated payment /NS&I’s modernisation programme: A £3bn lesson in how to lose public trust /Resilience under pressure: How regional conflict is reshaping the Middle East tech strategy /NCSC: No increase in cyber threat from Iran, but be prepared /NS&I seeks Bank of England counsel over project disaster /MPs launch inquiry into use of tech in education /Is a social media ban for under-16s proportionate? /
Delivery comms, intelligent fulfilment, and AI’s growing influence /Iranian hacktivists muster their forces but state APTs lay low /Zero-day in Android phone chips under active attack /Tycoon2FA phishing platform dismantled in major operation /UK lab gets funding to drive foundational AI research /Landmark legal challenge against Home Office eVisa system heard /Is there no stopping the AI spending spree? /Civil service veteran ‘incandescent’ as wait for pension hits four months amid outsourcing mess /AI workloads force a fundamental redesign of Middle East datacentres /Transnational AI regulation needed to protect human rights in the UK /National Grid, Nebius and Emerald hail datacentre power throttling /Interview: Wolf & Badger CEO George Graham on getting ‘hands-on’ with AI /Open cyber standards key to cross-platform integration /Santander and Mastercard complete test of AI-initiated payment /NS&I’s modernisation programme: A £3bn lesson in how to lose public trust /Resilience under pressure: How regional conflict is reshaping the Middle East tech strategy /NCSC: No increase in cyber threat from Iran, but be prepared /NS&I seeks Bank of England counsel over project disaster /MPs launch inquiry into use of tech in education /Is a social media ban for under-16s proportionate? /
ABOUT
Hi I'm Kavi! Recent graduate of Bachelors in Technology in Artificial Intelligence & Data Science. I have been making video games from the age of 14, an experience that gave me strong foundations in computer science and design. I'm currently building AI native B2B SaaS Products and exploring the world of quantitative finance Some quick stats: - Developed 10+ video games - Finalist in 3+ national level hackathons - Served 10+ freelancing clients, valued $300-$5000 per project - Solved 475+ problems on leetcode
Resume.exe
Experience
Lyzr AI
Founder's Office Developer
Aug 2025 - Present | Bengaluru, India (Hybrid)
- Building SaaS applications powered by production ready Lyzr AI Agents
Quantegies
AI Engineer
July 2025 - Aug 2025 | CA, United States (Remote)
- Worked on areas such as quantitative finance, algorithmic trading and machine learning using C++

Teachafy Labs
Founding AI/ML Engineer
Dec 2024 - July 2025 | Chennai, India
- Designed & engineered the product to production, and setup CI/CD pipelines using Git, Docker Compose & AWS
- Ensured 100% consistency integrating 3rd party platforms such as Notion & Frappe, using a two-way database sync system
- Awarded Most Valuable Player of the organization, for completing a four-month project in one month
- Technologies Used: OpenAI Assistants API, Google Agent Development Kit, LangChain, FastAPI, PostgreSQL, Docker Compose, AWS, Composio, Notion, Frappe, Supabase, DevOps, CI/CD

Fiverr
Freelance Full Stack Developer
Dec 2023 - Nov 2024 | Remote, Global
- Delivered 5+ client websites using SvelteKit with 100% on-time completion, and $1.2K revenue in 2 weeks
- Deployed frontend websites with 95-97% mobile performance using optimizations such as caching, lazy loading and splitting

Cognizant
Research & Development Intern
Jun 2023 - Aug 2023 | Chennai, India
- Reduced warehouse navigation time by 50% for clients by innovating an AR navigation app (for Vuzix m400) using Unity3D
- Optimized pathfinding algorithms to enable error-free routing in complex environments, boosting client productivity
- Presented a demo to the President EMEA of Cognizant following internal recognition by high-level executives for work
Selected: Experience
5 Items
Welcome to my
Video Game Universe
VIDEO GAMES
I craft rich purpose driven experience that shares a story, dive into my video game universe! Check out my games at dataoverflow.itch.io
WEB PROJECTS
Check out my high performance fullstack projects here
[ ■ ]
All Projects
Open Project (Scroll)
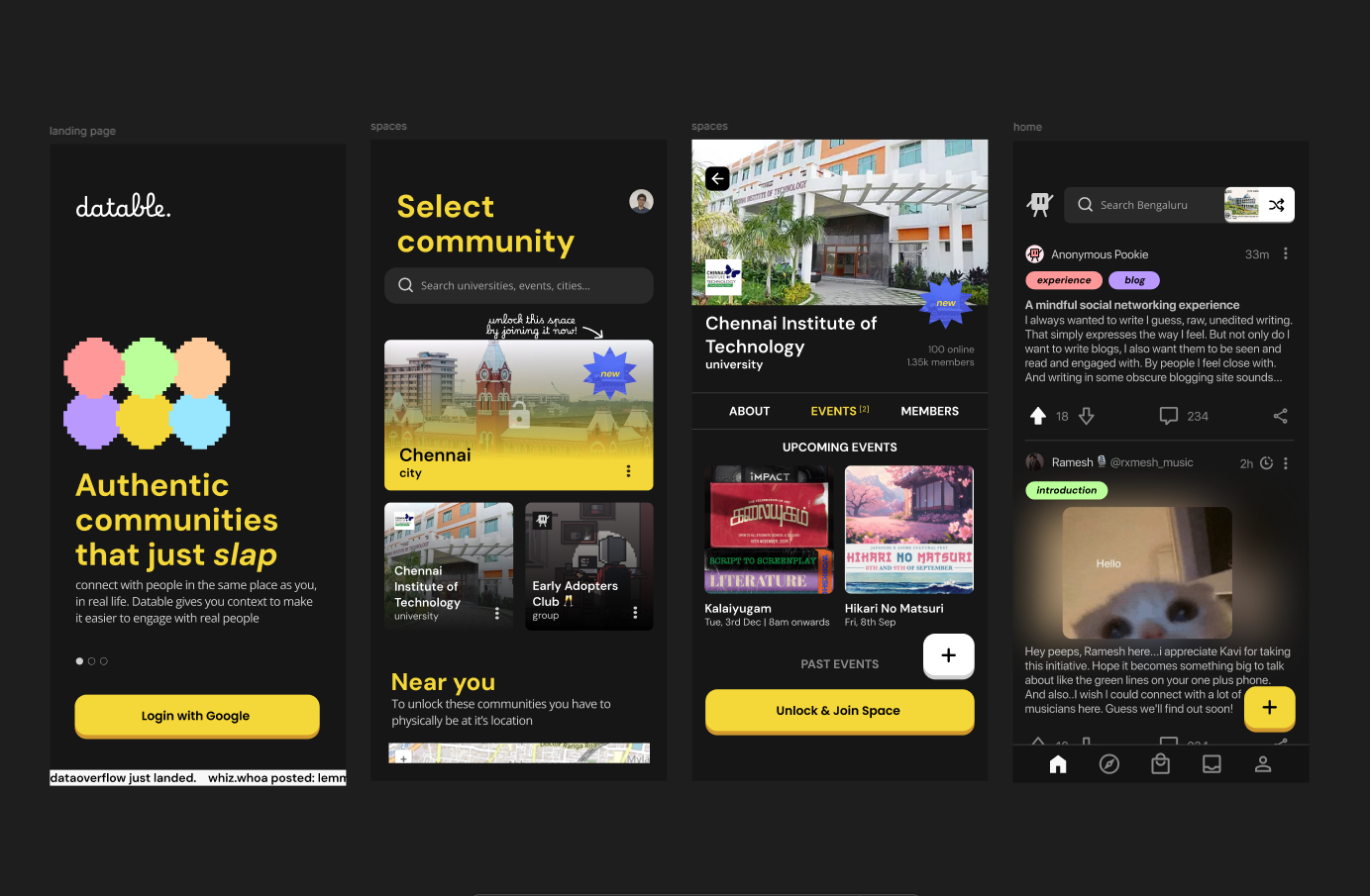
DATABLE - GEOLOCATION SOCIAL APP
SvelteKit 5, Tailwind CSS, Capacitor, Pocketbase, GCP, Docker
Built a community driven platform to augment real life places or events, implementing a recommeder system to meet people. Achieved 99.9% uptime using Docker and GCP, enabling real-time interactions for 100+ active users on the app.
ExploreC:\TURBOC3\BIN\PROJECTS\*CPP
DATABLE.CPP
2024